Zendesk Abuse: How cybercriminals are Weaponizing Customer Support Systems for Targeted Email Attacks
October 17, 2025 – A concerning vulnerability in the popular customer service platform, Zendesk, is being exploited by cybercriminals to launch sophisticated email attacks. These attacks don’t involve hacking into Zendesk, but rather leveraging a widespread configuration weakness within how its customers manage support requests.The result? Targeted individuals and organizations are being bombarded with menacing and disruptive emails appearing to originate from legitimate, well-known companies using the Zendesk platform.
Over the past week, KrebsOnSecurity experienced a deluge of these automated messages – thousands in a matter of hours. What made this attack especially alarming was the sheer number of compromised-looking senders: recognizable brands like CapCom, CompTIA, Discord, GMAC, NordVPN, The Washington Post, and even Tinder all appeared as the source of these unwanted communications.
what’s Happening? The Anatomy of the Attack
these aren’t phishing emails in the traditional sense. Instead, the attackers are exploiting Zendesk accounts configured to allow anonymous users to submit support tickets without email verification. This seemingly convenient feature – intended to lower barriers to customer support – has become a gaping hole for abuse.
The attackers are crafting tickets with malicious or harassing subject lines. In my case, the messages ranged from false claims of law enforcement investigations to outright personal insults. Crucially, as Zendesk is configured to automatically send ticket creation notifications, these messages are being blasted out to the target’s inbox, appearing to come directly from the compromised company’s email domain.
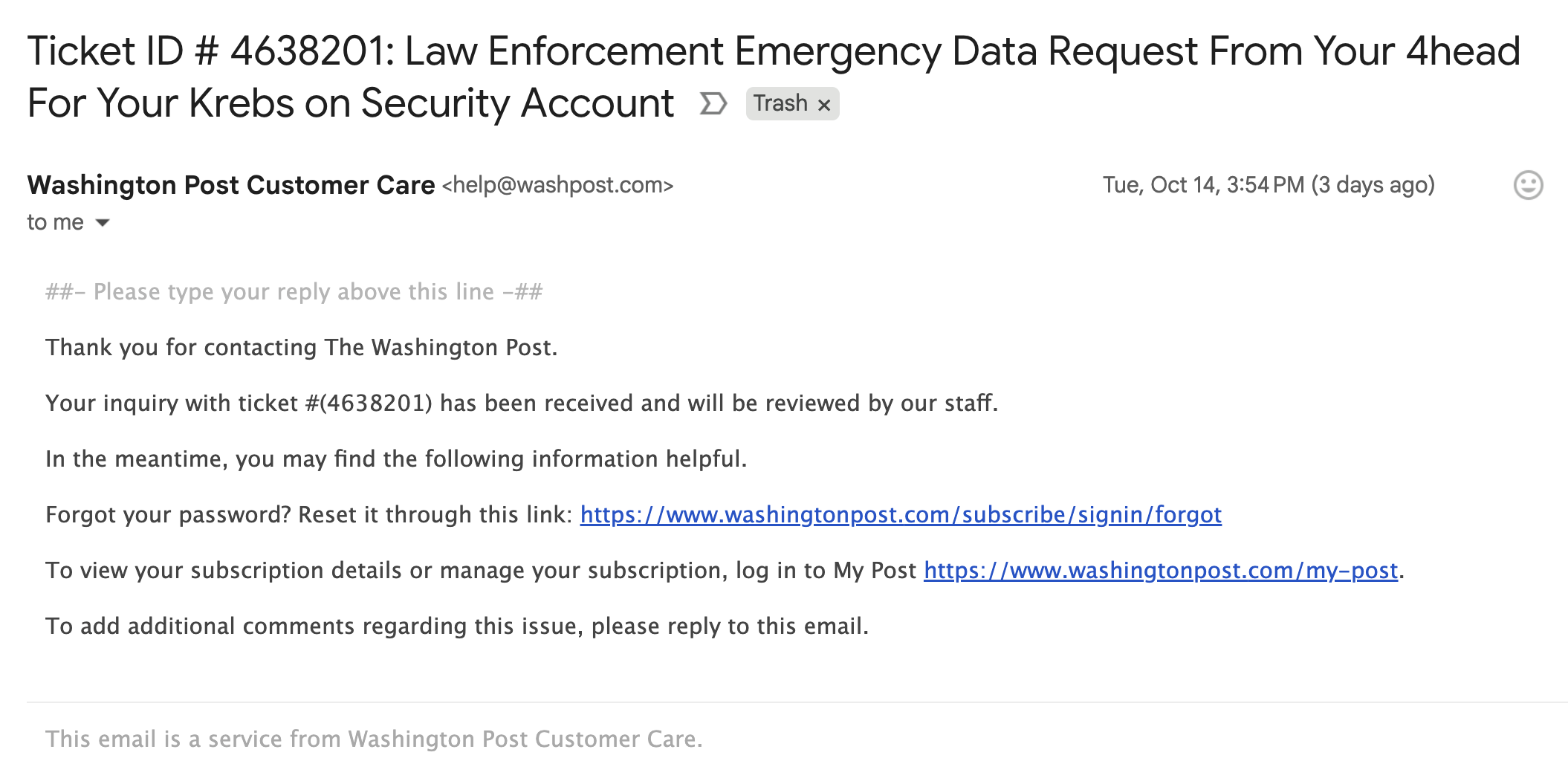
Take,such as,a message appearing to originate from The Washington Post’s Zendesk installation. A simple reply reveals the reply-to address is a legitimate Washington Post email: help@washpost.com. This isn’t a spoofed email address; it’s a genuine notification sent through their system.
[Image of example message from The Washington Post, as provided in the original article, with caption: “An example of one of the numerous messages received this week, appearing to originate from The Washington Post’s Zendesk support system.”]
Why is This Happening? A Balancing Act Between Convenience and Security
Zendesk acknowledges the issue.According to Carolyn Camoens,Communications Director at Zendesk,the ability to accept anonymous tickets is a deliberate feature.
“These types of support tickets can be part of a customer’s workflow,where prior verification isn’t required to allow engagement with support capabilities,” Camoens explained. “While we recommend authenticated ticket creation, some customers prefer an anonymous habitat for various business reasons.”
The problem lies in the fact that anonymous submissions also allow attackers to specify the email address the notification is sent to. This allows them to flood a target with messages appearing to come from numerous legitimate sources.Zendesk’s auto-responder, triggered by ticket creation, then amplifies the attack by sending notifications from the customer’s domain.
While Zendesk has implemented rate limits to curb the volume of requests, these haven’t been sufficient to prevent the coordinated, “many-against-one” attacks we’ve observed.
What Does This Mean for Businesses and Individuals?
This incident highlights a critical security trade-off.While making customer support easily accessible is important, failing to validate email addresses before sending automated responses creates a meaningful vulnerability.
Here’s what’s at stake:
* Brand Reputation Damage: Having yoru company’s name associated with harassing or malicious emails can severely damage your brand’s reputation and erode customer trust.
* Disruption and Annoyance: The sheer volume of these messages can be incredibly disruptive and frustrating for recipients.
* Potential for More Sophisticated Attacks: While this current wave is primarily focused on harassment, the same technique could be used to deliver more targeted phishing attempts or spread misinformation.
What’s being Done? Zendesk’s Response and Mitigation Strategies
Zendesk is actively investigating additional preventative measures and advising customers to implement stronger security practices.Specifically, they recommend configuring Zendesk to require authentication for ticket creation.
“We recognize that our systems where leveraged against you in a distributed manner,” Camoens stated. “We are advising customers experiencing this activity to follow our general security best practices and configure an authenticated ticket creation workflow.”
Protecting Yourself and Your Organization
Here are some steps you can take to mitigate the risk:
* For Zendesk Customers: Instantly review your Zendesk configuration and require email verification for all
![Cork Flood Protests: Calls for Improved Defences Grow | [Year] Update Cork Flood Protests: Calls for Improved Defences Grow | [Year] Update](https://i0.wp.com/www.rte.ie/images/0023565a-1600.jpg?resize=150%2C150&ssl=1)
![WWE SmackDown Spoiler: Possible Return of [Star’s Name] Tonight! WWE SmackDown Spoiler: Possible Return of [Star’s Name] Tonight!](https://i0.wp.com/cdn-cache.wrestlingnewssource.com/u/webp/8be4db2ab8ef69cd78ec19ff68fd97e1_1200_675.webp?resize=150%2C150&ssl=1)





![Veterinary Care in [Country]: Training, Drug Regulations & Law Updates Veterinary Care in [Country]: Training, Drug Regulations & Law Updates](https://i0.wp.com/images.dailynewsegypt.com/2025/12/WhatsApp-Image-2025-12-24-at-2.32.11-PM.jpeg?resize=150%2C100&ssl=1)

