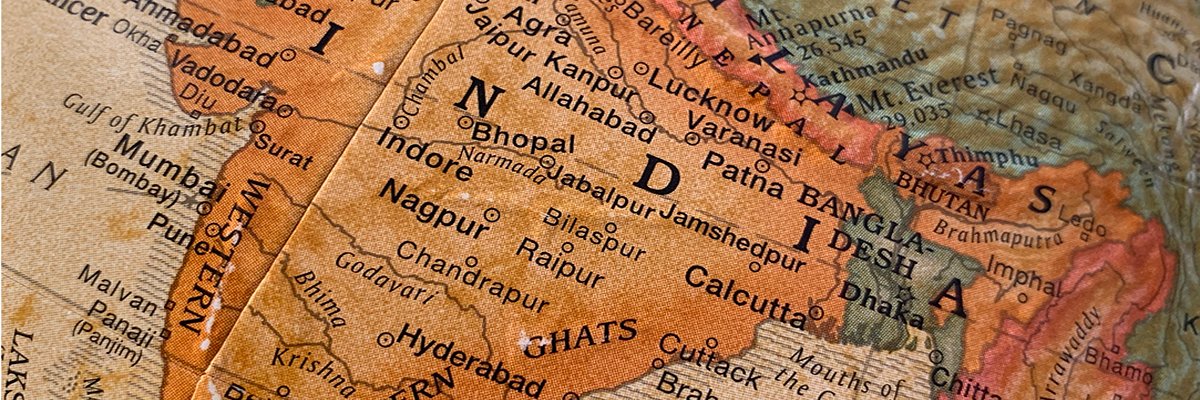
India’s Supply Chain: A Growing Cyber Risk for Global Businesses
Global supply chains, increasingly reliant on interconnected networks, face a significant and escalating threat: vulnerabilities within third-party suppliers in India. Recent research indicates a concerning trend – over half of Indian companies experienced a security breach in the last year – posing a significant risk to organizations worldwide.this isn’t merely a regional issue; it’s a systemic challenge demanding immediate attention and proactive mitigation strategies.
The Scope of the Problem: Widespread Weaknesses
A thorough report by SecurityScorecard reveals a landscape of security weaknesses across diverse Indian sectors. These aren’t limited to smaller, less-protected entities. The study highlights vulnerabilities within manufacturers supplying critical industries like aerospace and pharmaceuticals,alongside IT services firms that form the backbone of global digital infrastructure.
The findings are stark: the security posture of Indian suppliers is demonstrably weaker than initially anticipated, creating a potential cascade effect where a single breach can ripple outwards, impacting organizations across continents. While Indian IT service providers generally maintain a strong security baseline, thay sadly recorded the highest number of actual breaches within the study’s sample.This paradox underscores the inherent risks associated with their central role and complex operational environments.
Why India? The Unique Challenges
india’s prominence as a global IT and manufacturing hub makes it a particularly attractive target for cybercriminals. Globally, IT providers are inherently vulnerable due to their expansive attack surfaces and the privileged access they grant to third parties.However,India’s specific position within the global supply chain amplifies these risks.
The report details a surge in malicious activities targeting Indian IT companies,including:
* Typosquatting: The registration of deceptively similar domain names to trick users into visiting malicious websites.
* Credential Compromises: The theft and misuse of login credentials, granting unauthorized access to sensitive systems.
* Infected Devices: The proliferation of malware-infected devices within supplier networks.
Crucially, the study found that suppliers providing outsourced IT operations and managed services accounted for a staggering 62.5% of all third-party breaches in the Indian sample – the highest proportion SecurityScorecard has ever documented.This statistic is a critical wake-up call for businesses heavily reliant on Indian IT vendors.
Beyond Third Parties: The Expanding Threat Surface
The risk doesn’t stop with direct supplier relationships. Indian companies themselves operate within a complex web of fourth-party relationships – the suppliers of their suppliers. this creates an exponentially expanding threat surface. A single ransomware incident or disruptive cyberattack affecting a seemingly minor Indian vendor coudl have devastating consequences,halting production lines,delaying critical service delivery,and disrupting global logistics networks.
Ryan Sherstobitoff, Field Chief threat Intelligence Officer at SecurityScorecard, emphasizes the gravity of the situation: “India is a cornerstone of the global digital economy. Our findings highlight both strong performance and areas where resilience must improve. Supply chain security is now an operational requirement.”
A Global Pattern: The Rise of Third & Fourth-party Breaches
The vulnerabilities within the Indian supply chain aren’t isolated.SecurityScorecard’s research reveals a broader global trend. A separate report found that 96% of Europe’s largest financial services organizations have been impacted by a security breach at a third-party supplier.Even more concerning,97% have experienced a breach via a fourth party,a significant increase from 84% just two years ago.
This escalating pattern demonstrates a clear and present danger: organizations are increasingly vulnerable to attacks originating not directly from their own systems, but from the interconnected network of suppliers they rely upon.
mitigation Strategies: Building a Resilient Supply Chain
Addressing this complex challenge requires a multi-faceted approach:
* Enhanced Due Diligence: Thoroughly vet all third-party suppliers, including a comprehensive assessment of their security posture. Don’t rely solely on self-assessments; autonomous verification is crucial.
* Continuous Monitoring: Implement continuous security monitoring of third-party systems to detect and respond to threats in real-time.
* Contractual Security Requirements: Establish clear and enforceable security requirements within contracts with suppliers, outlining expectations for data protection, incident response, and vulnerability management.
* Supply Chain Mapping: Develop a detailed map of your entire supply chain, identifying all third and fourth-party relationships.
* Incident Response Planning: Develop and regularly test incident response plans that specifically address supply chain breaches.
* Zero Trust Architecture: Implement a Zero Trust security model, verifying every user and device before granting access to sensitive resources.
* Cybersecurity Insurance:

![Aberdeen vs [Opponent]: Thelin’s Debut – Hope or More Frustration for Dons Fans? Aberdeen vs [Opponent]: Thelin’s Debut – Hope or More Frustration for Dons Fans?](https://i0.wp.com/ichef.bbci.co.uk/ace/branded_sport/1200/cpsprodpb/1704/live/42bc85c0-9be6-11f0-92db-77261a15b9d2.jpg?resize=150%2C150&ssl=1)






![Ulster Rugby Win: Murphy Reacts to Away Victory | [Season/Year] Ulster Rugby Win: Murphy Reacts to Away Victory | [Season/Year]](https://i0.wp.com/www.rte.ie/images/0023ad81-1600.jpg?resize=150%2C100&ssl=1)
